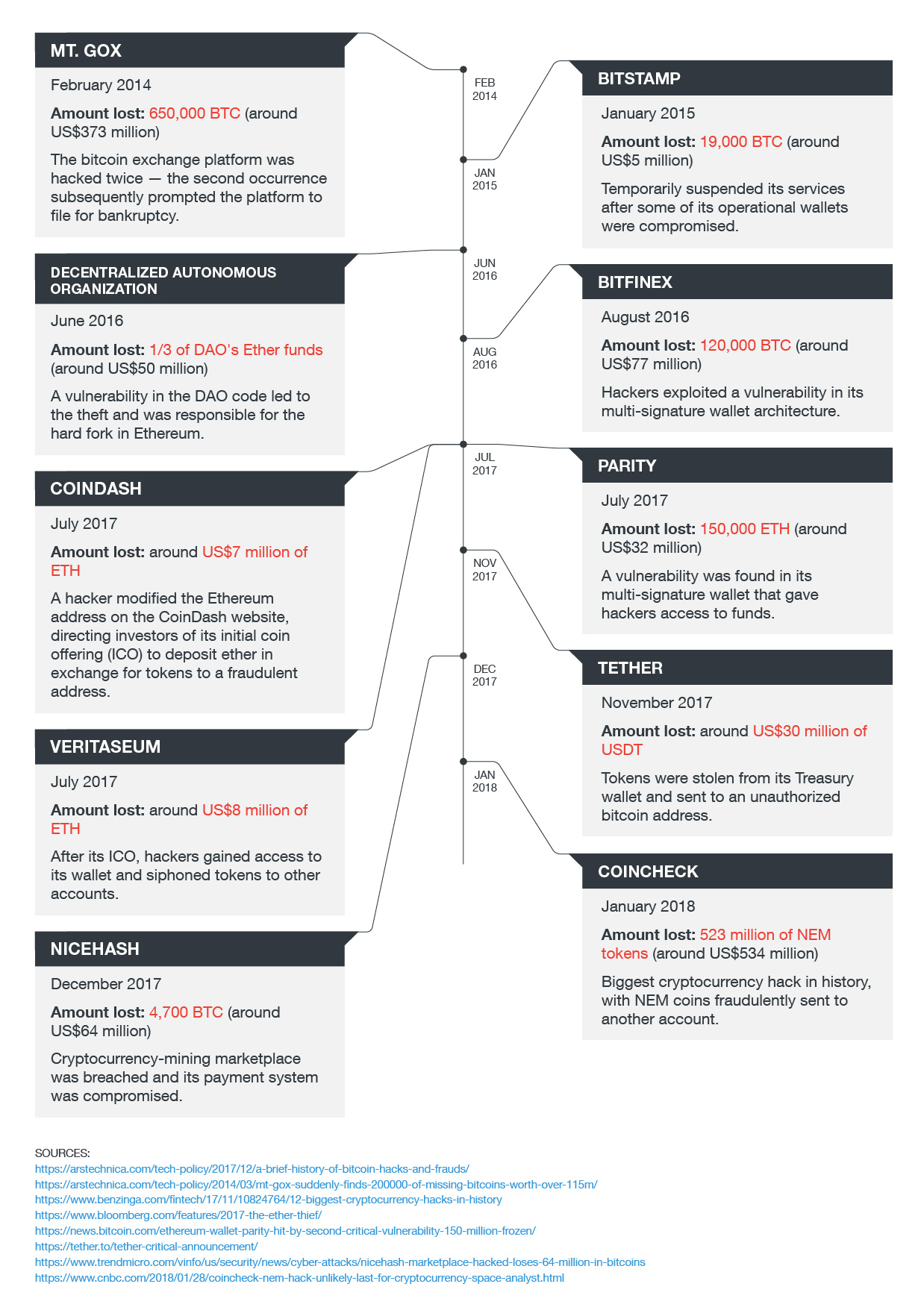
Routerpwn app, (a) list of router brands (b) list of vulnerabilities... | Download Scientific Diagram

High-impact vulnerability in DrayTek routers leaves thousands of SMEs open to exploitation | The Daily Swig

12-Year-Old Router Vulnerability Discovered Affecting Millions of Devices Exposing Serious Supply Chain Risks - CPO Magazine


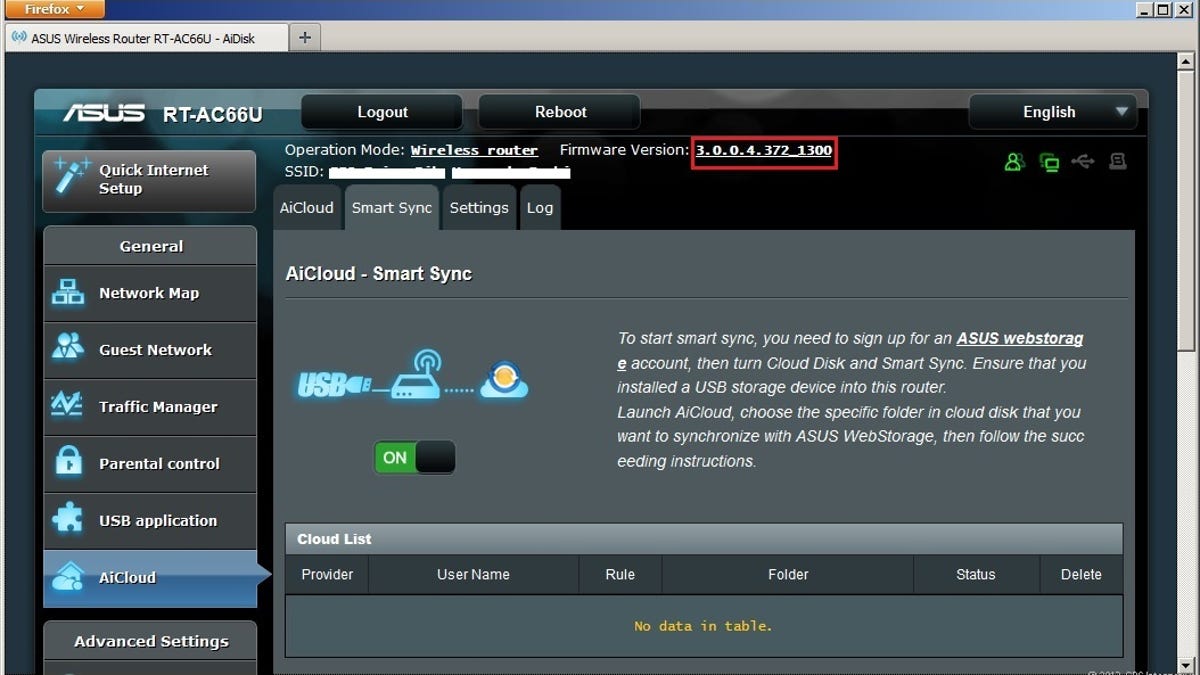
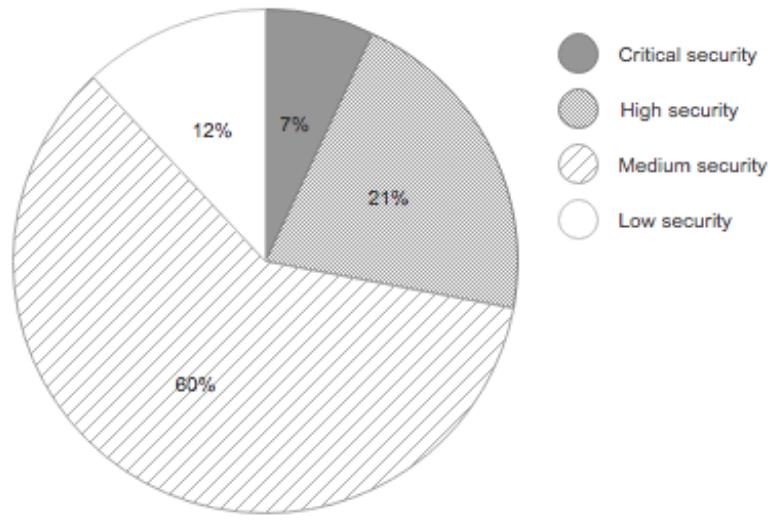



![Top 5 IoT vulnerability exploits in the smart home [list] Top 5 IoT vulnerability exploits in the smart home [list]](https://www.minim.com/hubfs/iot-vulns-feature-12.jpg)